Overview
Overview of Zero Trust Systems
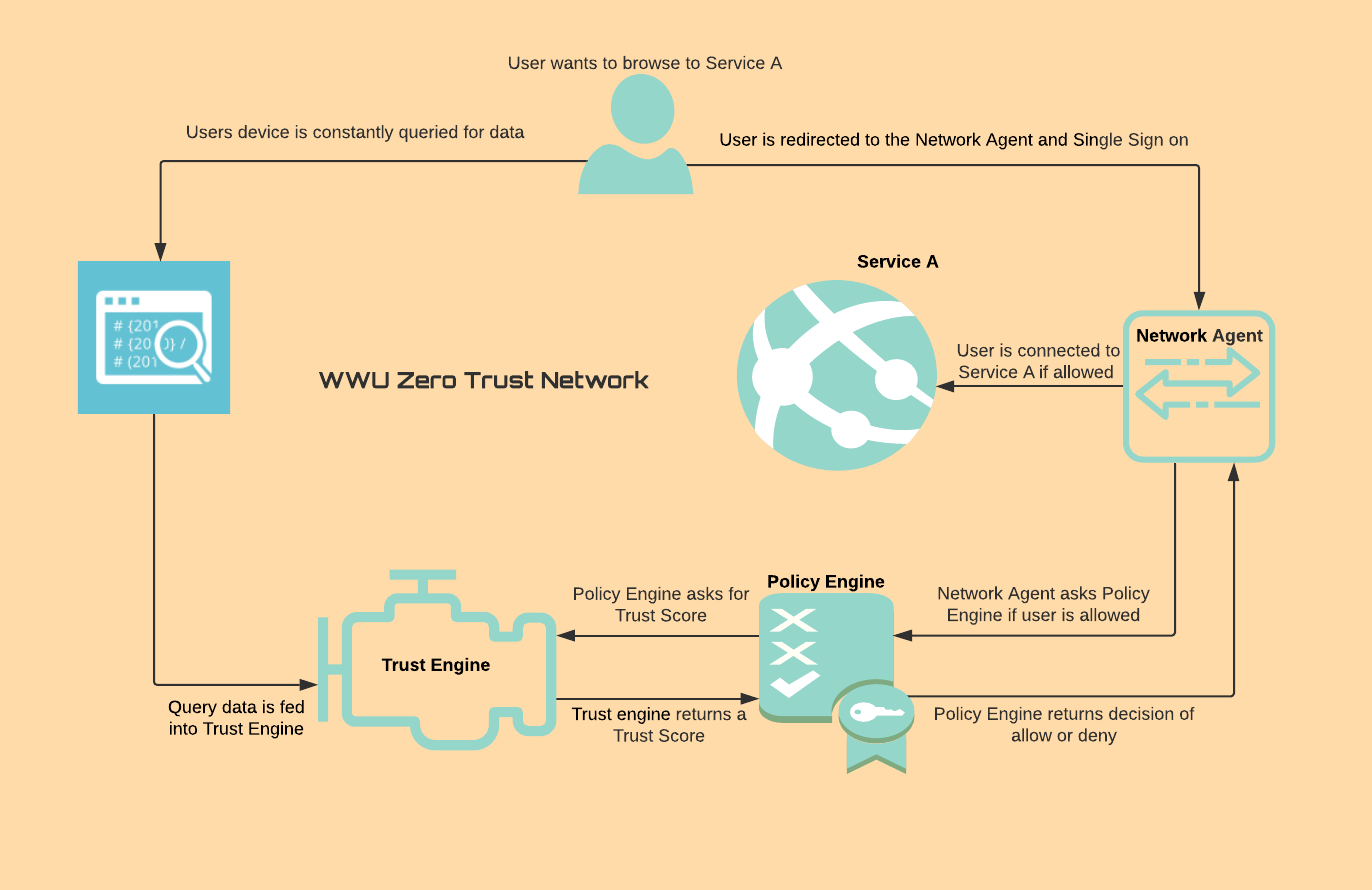
The flow of information travels in two directions from the user. The first is the osquery logs being delivered hourly to the Fleet server in order for the Trust Engine to determine a trust score. In the other direction the user is making an attempt to log into a secured application. If the user has not accessed this resources within a recent window then traffic will be redirected by the Network Agent to the Policy Engine where the Policy Engine will decide if the user is granted access based on the users trust score.
Zero Trust: Good Score Example
In this video we demonstrate our system working for a user with a high trust score. The end result is that the user will be allowed to access the secured application.
Zero Trust: Bad Score Example
In this video we demonstrate our system working for a user with a low trust score. The end result is that the user will be blocked from accessing the secured application.
Data Flow Overview
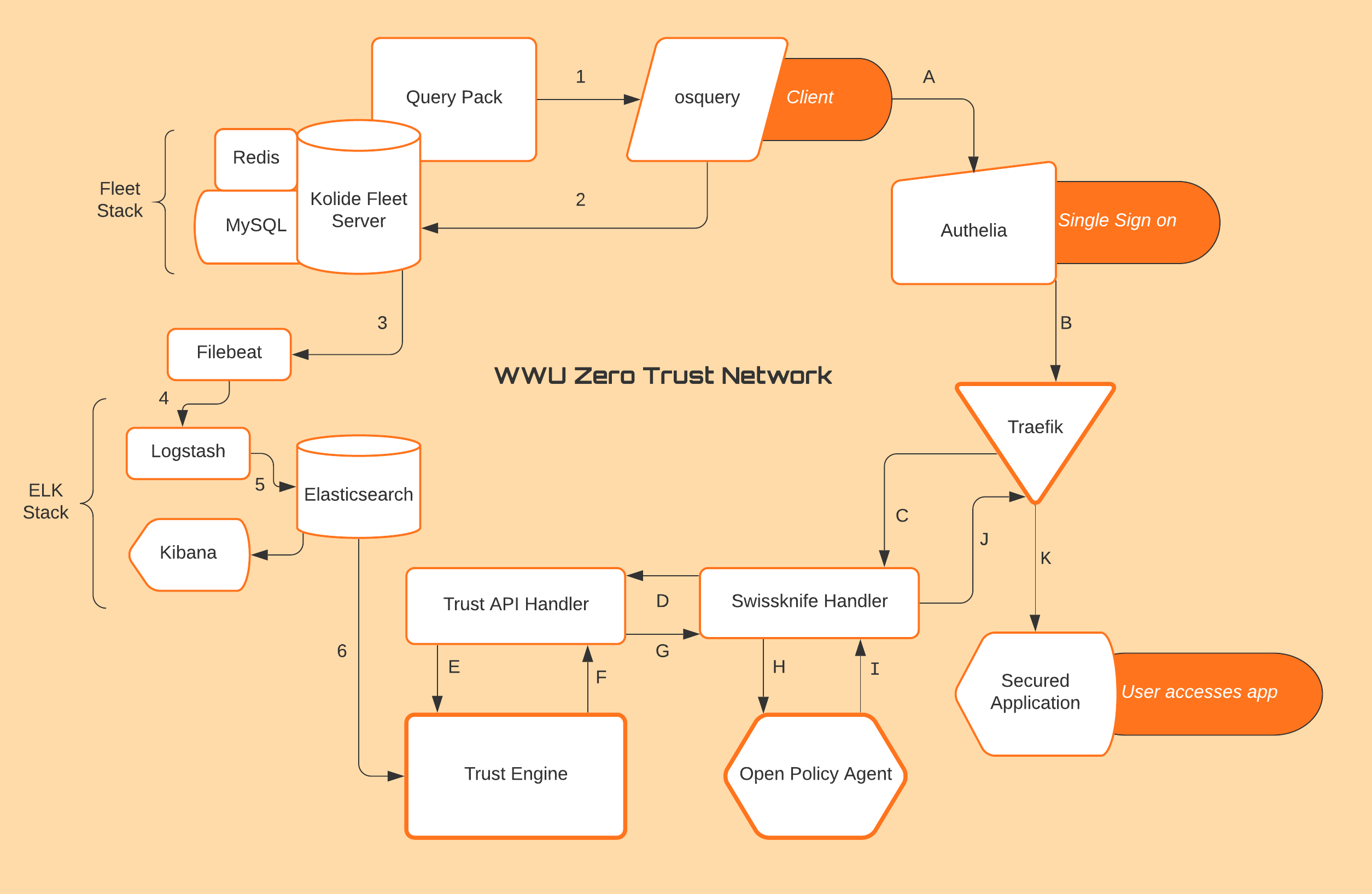
| 1. Kolide Fleet server runs a scheduled query pack on the client machine that already has osquery installed on it. | A. The users goes to log into the secured application and Authelia authenticates the user via their username and password. |
| 2. The queried data is delivered to the Kolide Fleet server. | B. After the user is authenticated the traffic is redirected the proxy service Traefik. |
| 3. Log file data from Kolide is shipped by Filebeat to Logstash. If there are multiple servers then each would have a Filebeat agent on it. | C.Traefik forwards the authorization of the request to the Swissknife Handler. |
| 4. Logstash aggregates the data received from Filebeat and sends it to Elasticsearch. | D. The Swissknife Handler accepts the username and the destination from Traefik and forwards the username to the Trust API Handler. |
| 5. Elasticsearch holds the JSON formatted data under the index: osquery-result-yyyy-mm-dd. The data can be viewed in Kibana. | E. The Trust API Handler sends the username to the Trust Engine. |
| 6. The Trust Engine ingests data from Elasticsearch and uses the query fields to determine a trust score. The Trust Engine only requests data from Elasticsearch when triggered by the Trust API Handler seeking validation of a specific user. | F. The Trust Engine computes a score and returns it to the Trust API Handler. |
| G. The Trust API Handler sends the score for that username back to the Swissknife Handler. | |
| H. The Swissknife Handler queries the Policy Engine (OPA) with the username, resource, and the score. | |
| I. The Policy Engine then makes a decision based on the defined policies. It will return allow or deny to the Swissknife Handler. | |
| J. The Swissknife handler takes this decision and returns it to Traefik. | |
| K. Traefik will send the user through to the secure application if it is allowed or respond with a 401 error if it is denied. |